Balancing a Data Governance Strategy: The Defensive-Offensive Framework
In today's data-driven landscape, organizations face a tough balancing act of protecting and securing data while simultaneously making it accessible and valuable. Understanding this inherent duality is the best way to internalize data governance in the form of a defensive-offensive framework.
Why does this matter now?
The stakes for getting data governance right have never been higher. Organizations are grappling with an exponential increase in data volume and complexity, while facing intensifying regulatory pressures and cyber threats. Simultaneously, the role for data to drive competitive advantage has become critical. Building on our previous discussion about The Rise of Modern Data Governance, we can now understand the practical challenge of balancing these competing demands. The companies that master this balance between protection and value creation will separate themselves from those that get stalled by either excessive controls or unmanaged risks.
Think of data governance as being pulled by two opposing forces. The defensive force is pushing, while the offensive force is pulling.
Understanding these forces - and how they interact - is kind of a cheat code for making informed governance decisions in any given situation.
In this second installment of The Datacraft Guide to Data Governance series, I'll break down:
- The defensive aspects: What they encompass and why they matter
- The offensive aspects: Their role in driving business value
- How these forces interact in different organizational contexts
- Ultimately, the million dollar question: How to craft a balanced governance strategy?
This post is not about prescribing specific implementations. Rather, it's about understanding the framework so you can better evaluate and balance competing demands in your own governance initiatives.
Whether you're revamping your data governance strategy or building one from scratch, this framework will help you evaluate and balance competing demands in your specific context.
The Dual Forces of Data Governance: An Overview
The framework is simple. At its core,
- Defensive Data Governance protects business value.
- Offensive Data Governance drives business value.
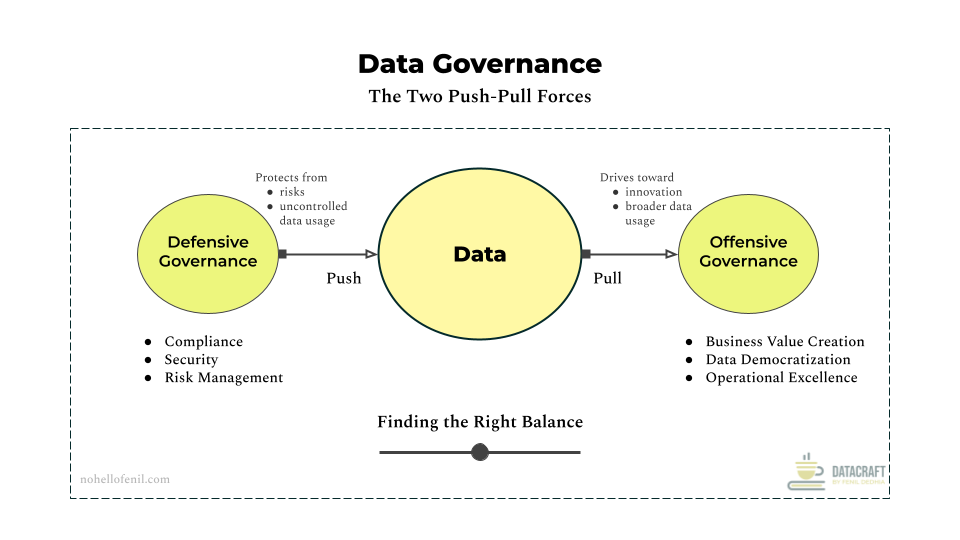
The "Defensive" Force of Data Governance
The defensive force emerges from the need to protect data assets and ensure compliance. This force pushes back against risks and uncontrolled data usage, acting as a necessary constraint on how data is handled and accessed.
The defensive force protects business value through three primary channels:
- Compliance:
- Industry-specific Regulations: From HIPAA in healthcare to BCBS 239 in banking, each industry brings its own regulatory demands
- Privacy Compliance Laws: Global requirements like GDPR and regional ones like CCPA shape how we handle personal data
- Audit and Reporting Requirements: Organizations must maintain detailed audit trails and documentation to demonstrate ongoing regulatory adherence
- Cross-Border Data Transfer: Strict protocols govern how data moves between jurisdictions, especially for transfers involving the EU and US
- Emerging Compliance Requirements: As data capabilities evolve, new compliance frameworks emerge to address novel risks
- Security: The foundation of protection - implementing controls, managing access, and safeguarding data throughout its lifecycle. While compliance tells you what to protect, security determines how to protect it.
- Risk Management: Beyond immediate security concerns, this involves anticipating threats, managing vulnerabilities, and maintaining data integrity across the organization.
The "Offensive" Force of Data Governance
The offensive force emerges from the need to create value from data. This force pulls organizations toward innovation and broader data utilization, driving the expansion of how data is leveraged across the business.
The offensive force drives business value through three primary channels:
- Business Value Creation: At the core of business value creation sits a comprehensive Data Quality Framework. Business value is created through outcomes like:
- Enabling both reliable decisions and innovative initiatives through trusted data
- Creating opportunities for data-driven growth and transformation through a Data-as-a-Product mindset.
- Supporting new data initiatives with comprehensive data quality frameworks, while maintaining appropriate guardrails.
- Building data quality through structured observability, monitoring, and remediation processes.
- Data Democratization: Making data accessible to those who need it while maintaining appropriate controls. The goal is empowerment without chaos through these three primary ways:
- Building trust through transparent quality metrics and certification
- Enabling collaboration between domain experts and technical teams
- Creating a shared terminology and understanding of data assets
- Operational Excellence: Mainly achieved through transforming how work gets done through well-governed data flows. This goes beyond efficiency to fundamentally improve how organizations operate, making processes more effective while reducing friction in data-driven activities. Some of the ways operational excellence can be scaled:
- Implementing continuous monitoring of data quality against business-defined rules
- Establishing remediation workflows that turn each issue into a learning opportunity
- Creating feedback loops between data quality incidents and process improvements
Each channel reinforces the others. Better-governed data enables more users to make better decisions, leading to improved operations and new opportunities for value creation. The idea is to maintain this forward momentum while ensuring appropriate controls remain in place.
💡 Now, let's examine each force in detail, starting with the defensive force that forms the foundation of any robust governance framework. Understanding these components will help you identify where to strengthen protection without creating unnecessary restrictions.

Defensive Data Governance
Think of defensive data governance as your organization's immune system - your data's very own Justice League.
It pushes back against risks and uncontrolled data usage by establishing the protection mechanisms that keep your data assets secure while ensuring you remain compliant with an ever-evolving regulatory landscape.
Compliance
1. Industry-Specific Compliance
Data governance helps organizations navigate a maze of industry-specific regulations. Whether it's HIPAA in healthcare, BCBS 239 in banking, or FERPA in education, each industry comes with its own regulatory demands.
In healthcare, HIPAA mandates strict controls over Protected Health Information (PHI). Consider a medical research institution that needs to share patient data with external researchers. Every data point must be carefully de-identified, access must be strictly controlled and logged, and any data transfers must be encrypted. This isn't just about having the right data; it's about proving it's being handled correctly.
2. Privacy Compliance Laws
Privacy regulations have evolved from simple guidelines to complex, enforceable laws with serious teeth. The GDPR set a new global standard when it launched in 2017, but it's just one piece of a growing privacy puzzle. From CCPA in California to the UAE's Personal Data Protection Law, organizations face an expanding web of privacy requirements.
In January 2024, France's privacy watchdog CNIL fined Amazon France Logistique €32 million for what it deemed an "excessively intrusive" employee surveillance system. The regulator found issues with how the company tracked employee scanner inactivity time and item scanning speeds, along with retaining this data for extended periods. This case demonstrates how compliance extends beyond customer data privacy to encompass employee privacy rights as well.
3. Audit and Reporting Requirements
Compliance often requires organizations to maintain detailed audit trails and generate reports demonstrating adherence to regulations. This includes documenting data access patterns, changes to sensitive information, and proof of required security controls.
4. Cross-Border Data Transfer Compliance
With global operations becoming the norm, organizations must navigate complex requirements for international data transfers. This includes understanding and implementing appropriate data transfer mechanisms, maintaining required documentation, and ensuring continued compliance as regulations evolve.
Example: When European companies store or process EU resident data in cloud services hosted in the United States, they must follow strict protocols. They need to implement Standard Contractual Clauses (SCCs), conduct transfer impact assessments, and maintain detailed documentation about their data protection measures. This often requires mapping data flows, assessing risks in the destination country, and implementing additional safeguards where necessary.
5. Emerging Compliance Requirements
While many compliance regulations exist, the transformative nature of data-driven industries dictates that new compliance regulations combat new threats, like advanced ransomware, and support new data methodologies. We'll get to those later.
Example: In 2021, the Social Media Privacy Protection and Consumer Rights Act of 2021 was introduced in the US, requiring social media platform operators to provide users with information about data collection and usage before creating an account.
Data Security
Consider a healthcare startup implementing role-based access control to manage patient data access. Their governance framework can ensure clinical staff see full patient records, billing staff access only financial information, and research teams work with anonymized data. The system can use data masking to show only the last four digits of social security numbers to billing staff while completely hiding them from research teams. Each access attempt can be logged and monitored, creating an audit trail of who accessed what data and when.
Strong security is about creating secure pathways for legtimate use. It's about implementing the technical and organizational controls that protect data throughout its lifecycle. When security controls are well-designed, they protect sensitive data while enabling authorized users to work efficiently.
Risk Management
A good risk management practice will address these 3 types of risks:
- Data Integrity Risks: Ensuring data remains accurate and untampered throughout its lifecycle
- Operational Risks: Managing the risks of data unavailability or system failures
- Reputational Risks: Protecting against data breaches and misuse that could damage trust
Consider a financial services firm addressing all three risk types through a comprehensive approach. For data integrity, they could implement validation checks and audit trails to ensure market data accuracy. For operational risks, they might discover analysts using personal email accounts to circumvent slow systems - leading them to improve system performance and provide secure file-sharing alternatives. For reputational risks, they could establish clear data handling protocols and monitoring systems to prevent unauthorized data sharing. This comprehensive approach can address both the immediate security risks and the underlying operational issues driving risky behavior.
Tackling risks holistically > just implementing restrictions.
Risk management should extend beyond immediate security concerns to encompass a broader view of potential threats to data assets. This includes identifying vulnerabilities, assessing their potential impact, and implementing controls to mitigate them.

Offensive Data Governance
Think of offensive data governance as your organization's growth engine - your data's X-Force.
It pulls organizations toward innovation and broader data utilization by establishing the frameworks and capabilities that transform data from a raw material into business value, while maintaining appropriate controls.
Business Value Creation
At the core of business value creation sits a comprehensive Data Quality Framework. This framework connects data quality with systematic observability, monitoring, and remediation capabilities.
Imagine a manufacturing company that transformed their sensor data from a compliance burden into a competitive advantage. By implementing a comprehensive data quality framework, they were able to enable plant managers to make reliable decisions about maintenance and resource allocation. This same governed data foundation could then power their data science team to develop AI-powered predictive maintenance. Because the data is already well-documented, validated, and accessible, they can focus on innovation rather than data preparation. The AI-powered predictive maintenance system can help prevent equipment failures and identifying optimization opportunities that significantly reduced energy consumption.
In healthcare contexts, companies could implement observability tools that continuously monitor patient demographic data quality. When the system detects a pattern of missing or inconsistent information, it could automatically trigger a remediation workflow. These quality improvements might then enable more accurate patient matching across systems, potentially reducing duplicate testing and improving care coordination. The organization could track how these quality improvements directly impact clinical outcomes and operational efficiency.
These examples illustrate how well-governed data becomes a trusted foundation for both everyday decisions and innovative initiatives. When data is of high quality, standardized, and certified, teams can focus on innovation rather than data preparation, accelerating the path from idea to value. Easier said than done.
Data Democratization
Data democratization can amplify the impact of operational excellence by tenfold!
It's one of the most rewarding transformations that you can pull off in any organizations. This is because the benefits of data democratization go beyond efficiency – it can transform how teams collaborate and serve customers. For instance, the product and consulting teams iterate faster on customer insights, making more data-driven feature prioritization, and quantifying customer success metrics without constantly requiring support from their data team.
Consider an educational institution implementing a self-service analytics platforms where faculty can access student performance data with clear quality indicators. The system could provide transparency into data lineage and quality metrics, building trust among users who might otherwise question the reliability of insights. When faculty members spot potential issues, they could contribute to quality improvement through collaborative feedback mechanisms.
Government agencies could implement data quality certification processes that visibly indicate which datasets meet rigorous quality standards. This approach could encourage broader use of high-quality public data while maintaining appropriate governance. Agency staff without technical backgrounds could confidently use certified data, knowing that quality monitoring and remediation processes are actively maintaining its accuracy.
For builders and consultants, data democratization is about striking the perfect balance between enablement and control. It's not just about providing access – it's about creating an environment where teams can confidently discover, understand, and use data in their daily work while maintaining security and compliance. This requires a balance of technology, processes, and culture.
Operational Excellence
Operational excellence focuses on establishing robust processes that maintain data quality throughout the data lifecycle. The higher the maturity of your operational excellence, the greater the benefits of offensive data governance that can be redeemed.
Consider a global enterprise standardizing their customer interaction data across regions. By implementing a governance framework that ensures consistent data capture and classification across different teams and channels, from sales to support, they can build a unified view of customer relationships. This can reduce duplicate efforts and help identify opportunities that were previously hidden in siloed systems.
Well-governed data enables both efficiency and predictability in operations. When data flows smoothly and reliably between systems, teams spend less time fighting data issues and more time creating value.
The sweet spot in data governance is where defensive guardrails enable offensive initiatives, creating an environment where innovation thrives within secure boundaries.
By treating data as a product with quality at its center, offensive data governance can transform how organizations create value from their data assets. The continuous quality improvement cycle - observe, monitor, remediate, improve business rules - creates a virtuous circle that progressively enhances data's business impact.
Striking the Right Balance
The key to effective data governance isn't choosing between these forces but orchestrating their interplay. Each force serves an essential purpose, and neither should dominate completely.
Consider these scenarios:
- When defensive forces overpower offensive ones, you get a "data vault" that stifles innovation and value creation
- When offensive forces run unchecked in pursuit of business value and operational goals, you risk security breaches and compliance violations
- The sweet spot is where defensive guardrails enable rather than restrict offensive initiatives
This balance isn't static - it shifts based on your organization's evolving context. You will need to recognize which force needs strengthening in your specific context, rather than prescribing a one-size-fits-all approach.
Good data governance looks much like a world-class nightclub - tight security at the door without the excessive wait, freedom to dance inside, and savvy bartenders who keep the right drinks flowing quickly to the right people. No bottlenecks, just smooth service and a great experience.
- Fenil Dedhia
Crafting Your Defensive-Offensive Strategy
Consider the following key questions to assess your current situation (not meant to be a comprehensive list):
Business Objectives
- What's your primary goal? Growth needs offensive focus, risk mitigation needs defensive strength. Growth phases might require amplifying offensive forces. Crisis periods could demand stronger defensive measures. A startup focusing on market expansion might emphasize offensive capabilities, while a company recovering from a data breach might need to strengthen defensive measures. New market entry might need both forces working in concert.
- What's your time horizon? Short-term compliance needs might require immediate defensive action. Companies preparing for IPO or entering new regulated markets need to prioritize defensive capabilities to meet compliance requirements.
- What resources do you have? Limited resources might need you to prioritize one force initially. An early-stage startup might focus first on defensive essentials before investing in risky bets that involve sophisticated data initiatives requiring more complex governance structures.
Industry Context
- How regulated is your industry? More regulations typically demand stronger defensive controls. For instance, healthcare or finance industries require leaning more on defensive governance due to HIPAA and BCBS 239 regulations.
- What's your competitive landscape? High competition might require stronger offensive capabilities. Technology companies often lean toward offensive forces to drive rapid innovation and maintain market position.
- What's your data sensitivity level? Higher sensitivity needs robust defensive measures. Companies handling personal health information or financial data need stronger protective measures than those dealing with public data.
Organizational Maturity
- How established are your data practices? New initiatives might need defensive foundations first. Organizations just beginning their data journey should focus on establishing secure data handling practices before pursuing advanced analytics. Early-stage companies will likely need to establish defensive foundations first. Mature organizations can push offensive initiatives with established controls. Legacy companies often need to strengthen offensive forces to modernize.
- What's your current data infrastructure? Legacy systems might need offensive modernization. Organizations with siloed, outdated systems often need to strengthen offensive capabilities to modernize and integrate their data landscape.
- How data-literate are your teams? Lower literacy might need guided democratization. Teams new to data-driven decision making need structured access and training before implementing full self-service analytics.
The path to effective data governance isn't about choosing between protection and value creation – it's about orchestrating their interplay to serve your specific context. As data continues to grow in both volume and strategic importance, the organizations that thrive will be those that master this balance.
Whether you're establishing new data initiatives or evolving existing ones, the defensive-offensive framework provides a practical lens for making informed decisions.
Execution is everything. Start by understanding where you stand today, identify which force needs attention, and remember that this balance requires constant, thoughtful adjustment as your context evolves.

Member discussion